Traditional Cloud Model
Your sensitive data leaves your organization and travels to external servers for processing. You lose control the moment it crosses your boundary.
See exactly how applications come to your data instead of your data going to applications. It's simpler than you think, yet more powerful than traditional cloud.
Traditional Cloud Model
Your sensitive data leaves your organization and travels to external servers for processing. You lose control the moment it crosses your boundary.
The Problem: Data in motion = risk in motion. Every transfer, every API call, every sync is a potential exposure point.
The Solution: Data stays put, capabilities come to you. Zero exposure, maximum control.
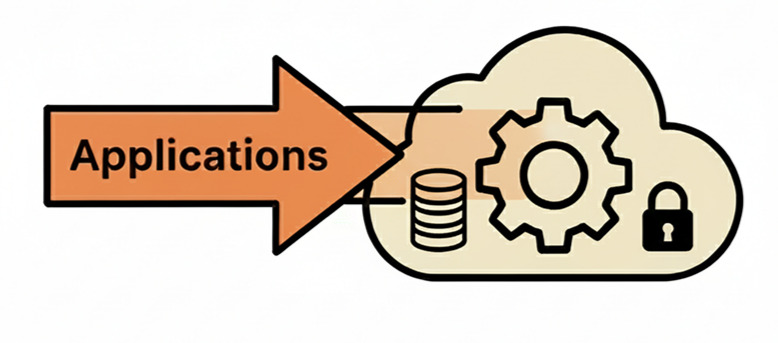
Bubl Cloud's Reverse Data Model
Applications and AI models come to your data. Processing happens where your data already lives. Your information never leaves your controlled environment.
Schedule a personalized demonstration where we'll show you exactly how applications deploy and run in your vault environment with your specific use cases.
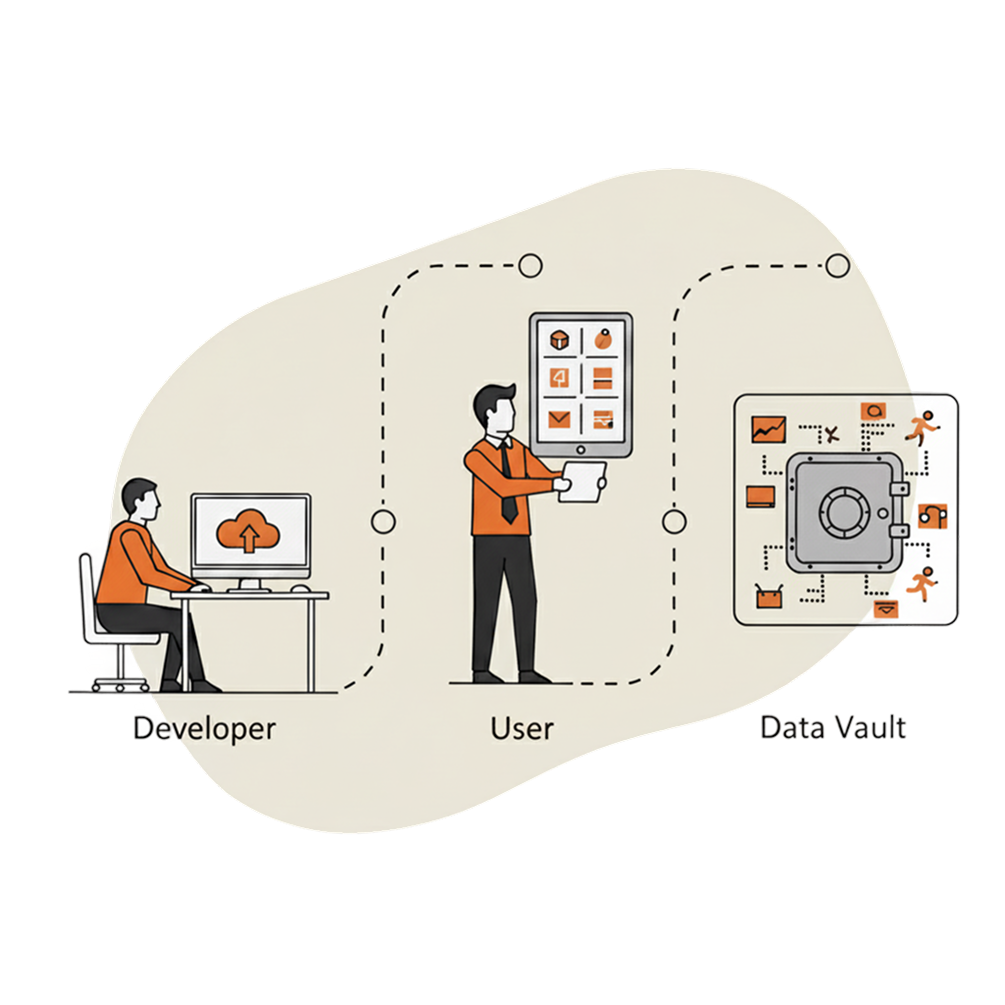
Step 1: Developers Upload Applications. Developers or your IT team upload applications via simple Docker containers to our application store. Any application that can be containerized can be made available - from AI models to business analytics tools.
Step 2: Select Your Applications. You or your users browse and select from the store which applications should run in the Data Vault. One-click deployment makes it as simple as installing an app on your phone.
Step 3: Secure Processing. Your selected applications run directly on your data without it ever leaving your Data Vault.
This ensures:
Start with a limited implementation to prove value with your specific data and applications - typically operational within 2 weeks.
Every application runs in its own isolated container within your vault. This provides security, scalability, and flexibility while maintaining simple management.
Applications can't interfere with each other or access unauthorized data unless you explicitly grant them access. When a new version of your application is uploaded data vaults using this application will automatically update.
Your vault comes with an application store - a marketplace where developers publish applications that can run securely in any Data Vault.

All applications uploaded to the store are isolated by default with zero external access. This ensures maximum security for your data and systems.
Even our technical team cannot access your data. The architecture is designed so that only your applications, running with your explicit permissions, can process your information.
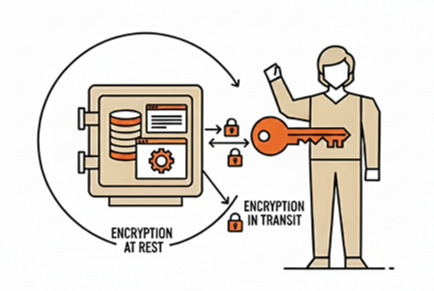
Your vault provides secure REST APIs that integrate seamlessly with existing systems while maintaining complete data protection.
Common Integrations:
Our solution architects will assess your current environment and design the optimal vault implementation strategy.
The most common questions about running AI applications in your own Data Vault, including data sovereignty, privacy protection, implementation and pricing are answered here.
The most common questions about running AI applications in your own Data Vault, including data sovereignty, privacy protection, implementation and pricing are answered here.
The most common questions about running AI applications in your own Data Vault, including data sovereignty, privacy protection, implementation and pricing are answered here.
The most common questions about running AI applications in your own Data Vault, including data sovereignty, privacy protection, implementation and pricing are answered here.
The most common questions about running AI applications in your own Data Vault, including data sovereignty, privacy protection, implementation and pricing are answered here.
Take the next step towards secure, sovereign AI processing. Your data stays protected while your capabilities expand.